
August 24, 2023
How to Use Cyber Asset Attack Surface Management (CAASM) Technology to Gain Complete Visibility of Assets
By Apexa iQ
Organizations are constantly adapting to the ever-changing digital world, and cloud technologies are becoming a popular choice due to flexibility, scalability, and cost-effectiveness. Managing and optimizing cloud resources can prove to be a demanding and time-consuming task. However, there is a solution to this problem - Cyber Asset Attack Surface Management (CAASM).
What is Cyber Asset Attack Surface Management (CAASM)?
Cyber Asset Attack Surface Management (CAASM) is an emerging technology that helps organizations gain a comprehensive view of their attack surface. This includes all of the assets, servers, network devices, endpoints, IoT devices, operating systems, application software, web applications, and databases on-prem, off-prem, or co-located, as well as the relationships between those assets. CAASM can be used to identify and mitigate security risks, improve compliance, and make better decisions about asset investments and deployments.
CAASM enables organizations to quickly respond to changing demands and ensure efficient resource utilization. It strengthens security and compliance by automating security configurations and monitoring.
CAASM solutions typically collect data from a variety of sources, including asset inventory tools, vulnerability scanners, and cloud management platforms. This data is then used to create a map of the organization's attack surface, which can be used to identify and prioritize vulnerabilities. It automates various aspects of cloud management, such as service provisioning, management, and optimization, which simplifies and accelerates the process. It allows organizations to maximize the benefits of cloud computing while improving operational efficiency and agility.
Benefits of CAASM for Cybersecurity
CAASM can offer numerous advantages to your organization, but its most crucial benefit lies in its ability to aid in the monitoring, evaluation, and minimization of your organization's entire attack surface. Following are 8 other benefits of CAASM for cybersecurity that you probably don’t know about.
- Benefit 1: Ensures consistent implementation while reducing the risk of misconfigurations and vulnerabilities by automating the deployment and configuration of security controls in the cloud.
- Benefit 2: Provides real-time alerts and reports to proactively address compliance issues by scanning cloud resources for non-compliant technology assets.
- Benefit 3: Minimizes the impact and time to mitigate threats by integrating with security incident management tools to automate incident response workflows, facilitating faster detection, investigation, and remediation of security incidents.
- Benefit 4: Provides security logs, event collection, and analysis from cloud resources with real-time monitoring of threats and abnormalities within your environment to detect and respond promptly.
- Benefit 5: Scales security controls to match the demands of cloud resources, adapting to changing needs of the environment and maintaining protection without unnecessary resource consumption.
- Benefit 6: Mitigates the risk of vulnerabilities and ensures organizations stay up to date with the latest security fixes by automating patch management processes to remediate vulnerable technology assets.
- Benefit 7: Simplifies security management and ensures consistency in a unified platform to manage security controls, policies, and configurations, while offering a holistic view of security posture.
- Benefit 8: Facilitates compliance assessments by generating comprehensive reports for audits and regulatory requirements, providing documented evidence of security configurations, controls, and compliance measures.
CAASM Vs. Other Solutions
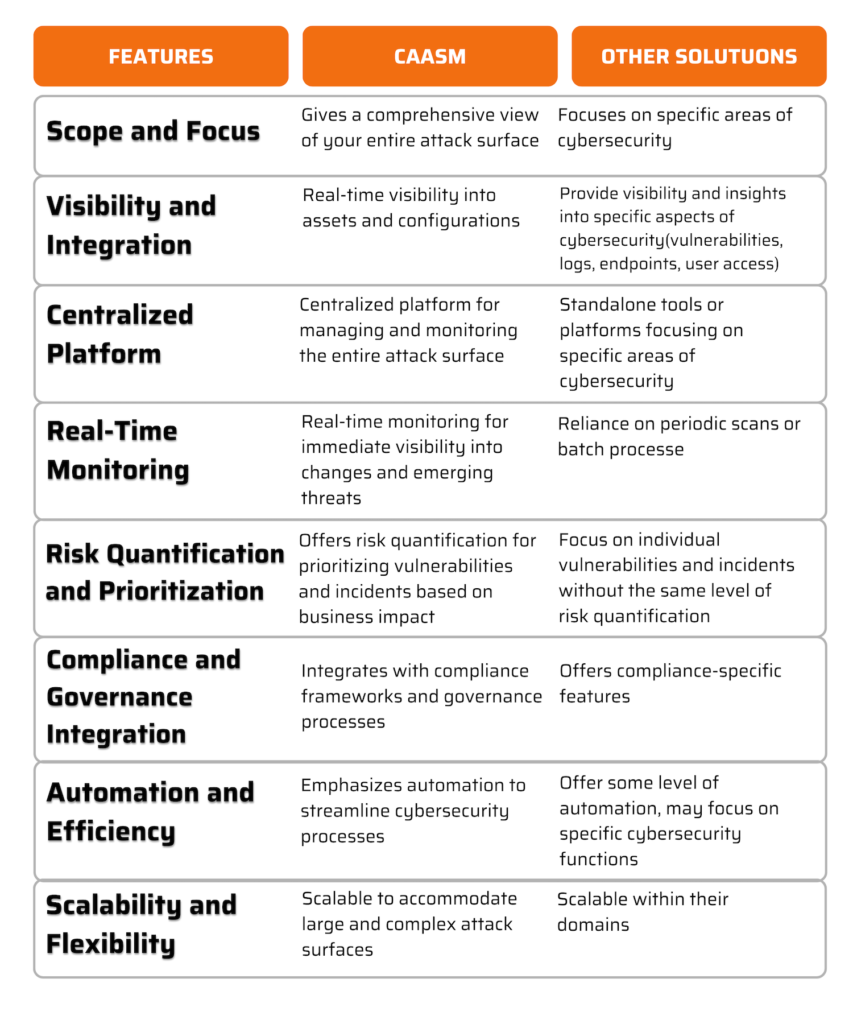
Using CAASM for Vulnerability and Incident Response
Incorporating CAASM into vulnerability and incident response strategies is essential for robust cybersecurity practices. CAASM offers organizations real-time visibility into their attack surface by empowering proactive vulnerability management, automated scanning, and effective incident detection and response. By harnessing CAASM's capabilities, organizations can bolster their security defenses, mitigate risks, and swiftly respond to emerging threats to protect critical assets and data.
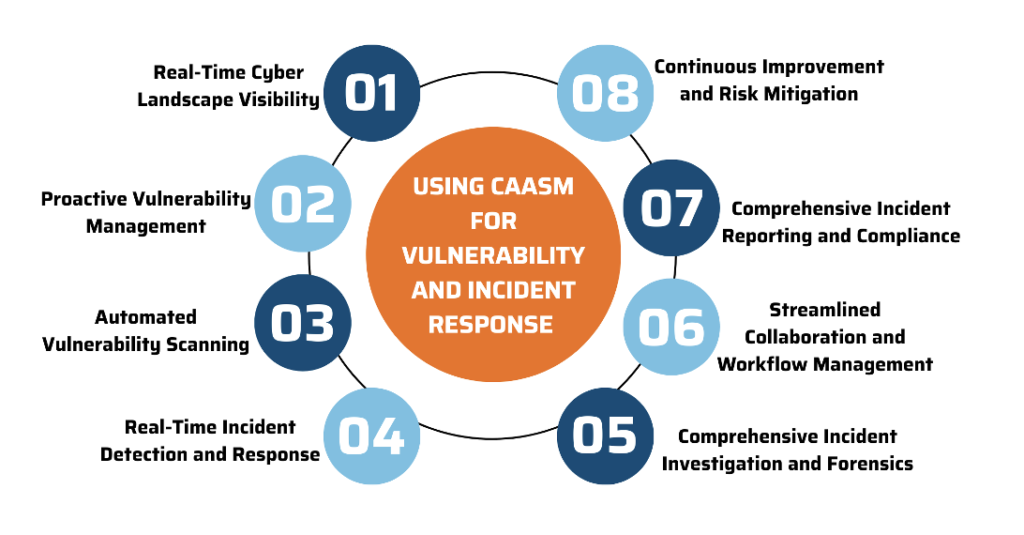
- Real-Time Cyber Landscape Visibility: Gain complete, real-time visibility into the organization's cyber landscape, including assets, configurations, and their relationships.
- Proactive Vulnerability Management: Empower your organization to proactively manage vulnerabilities by integrating vulnerability data with asset information for a complete picture of your cyber-attack surface.
- Automated Vulnerability Scanning: With automation, continuously monitor systems for vulnerabilities with efficient and effective remediation processes.
- Real-Time Incident Detection and Response: Quickly detect incidents as they occur in real-time by matching security events with assets and configurations.
- Comprehensive Incident Investigation and Forensics: Provide a comprehensive historical record of asset configurations and changes for incident investigation and forensics.
- Streamlined Collaboration and Workflow Management: Coordinate activities, assign tasks, and track progress for effective incident resolution process.
- Comprehensive Incident Reporting and Compliance: Implement incident reporting capabilities for compliance with industry regulations like General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), The Health Insurance Portability and Accountability Act (HIPAA), and Federal Deposit Insurance Corporation (FDIC).
- Continuous Improvement and Risk Mitigation: Proactively analyze trends, identify recurring vulnerabilities or incidents, and implement measures to enhance their overall security posture and mitigate risks.
Cloud Security and CAASM
By implementing CAASM, organizations can gain a holistic view of their cloud environment, enabling them to identify vulnerabilities, proactively respond to incidents, and ensure compliance with industry regulations.
This proactive approach to cloud security enhances the organization's resilience, protects sensitive data, and instills confidence with stakeholders. With CAASM, organizations can confidently embrace cloud technologies while maintaining a strong and secure infrastructure.
- Complete Visibility: Gain real-time visibility into your entire cloud attack surface, including assets, configurations, and relationships. This empowers effective monitoring, vulnerability identification, and threat detection for cloud infrastructure.
- Continuous Monitoring: Enable proactive identification of any changes or emerging vulnerabilities through continuous monitoring of cloud infrastructure. This approach allows organizations to detect and respond to security risks in real-time, minimizing the window of exposure to potential threats.
- Cloud Asset Management: Facilitate effective tracking and control of cloud resources, ensuring the security and integrity of the cloud environment.
- Configuration Assurance: Ensure proper configuration and adherence to security best practices for cloud assets. It automates checks and validations, guaranteeing consistent security configurations across the cloud infrastructure.
- Vulnerability Assessment and Remediation: Integrate vulnerability scanning capabilities to identify and address cloud vulnerabilities. Conduct regular vulnerability assessments and prioritize remediation efforts based on the criticality and potential impact of vulnerabilities.
- Incident Detection and Response: Swiftly identify and respond to security incidents, minimizing the impact and potential damage caused by attacks.
- Compliance and Governance: Gain comprehensive reporting and auditing features, ensuring adherence to security standards and facilitating compliance assessments.
- Scalability and Flexibility: Enable security measures to grow alongside the organization's cloud expansion.
With CAASM, you can discover, monitor, and prioritize your assets across your entire network, cloud, and IoT environments.
If you want to learn more about how CAASM technology can help you see and protect your assets, contact us today. Don’t wait until it’s too late - act now and secure your cyber assets with Apexa iQ. www.apexaiq.com/demo


