September 18, 2023
Complete Guide to Technology Asset Management Compliance
By Apexa iQ
In today's technology-driven world, managing technology assets and complying with standards and regulations has become more crucial than ever before. With an ever-expanding ecosystem of hardware, software, and data, organizations must ensure that their technology assets are used efficiently and securely while adhering to relevant compliance standards.
What is Asset Management Compliance?
Asset management compliance requires organizations to manage their assets in line with specific business standards and industry regulations. Compliance involves adhering to relevant laws, internal policies, and rules set by authorities. If an organization does not comply with proper device management, these technology assets will become obsolete, creating non-compliance which can leave your organization vulnerable. By ensuring technology asset management compliance, organizations can experience a host of benefits, such as:
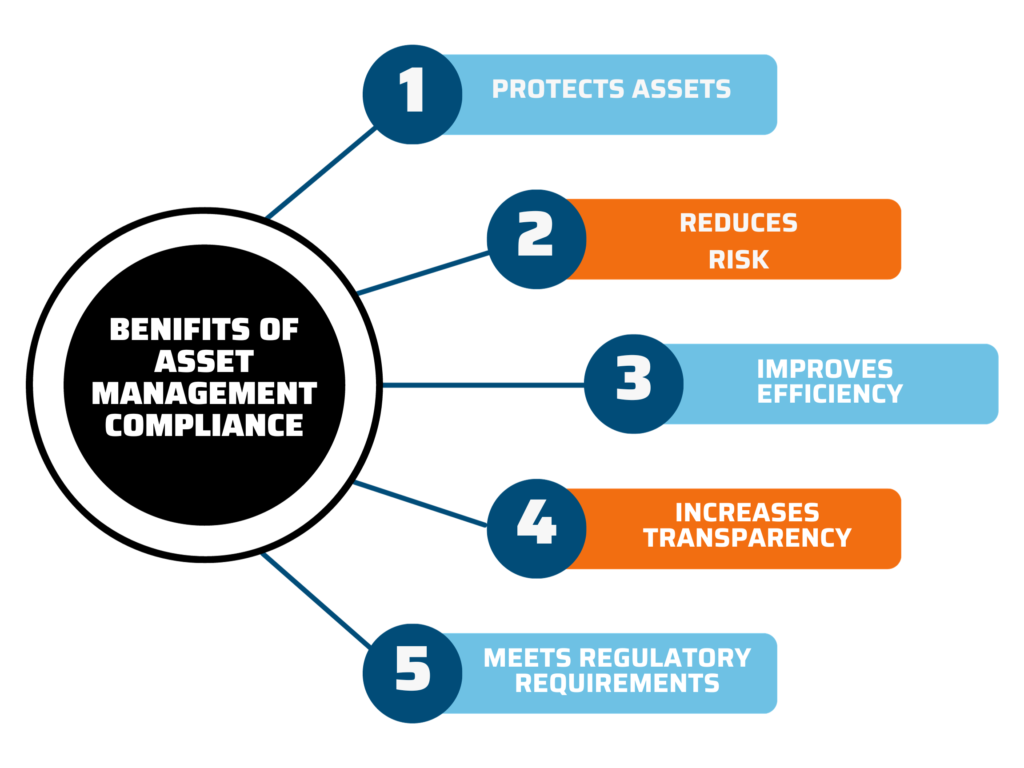
- Protects assets: Aids organizations in protecting their assets from loss, damage, or misuse with proper asset tracking and security measures.
- Reduces risk: Reduces the risk of financial loss, legal liability, and reputational damage in an organization by suitable security enhancement techniques.
- Improves efficiency: Improves the efficiency of asset management processes by deploying standardized processes, optimized asset lifecycle and resource allocation.
- Increases transparency: Increases transparency and accountability in asset management through clear documentation, real-time reporting, and audit trails.
- Meets regulatory requirements: Helps organizations navigate the complex landscape of regulatory requirements by customized compliance and change management.
What is Asset Management?
Asset management is the process of tracking and managing all of an organization's technology assets, from hardware to software to licenses, IoT and OT, and even assets that are cloud-based. The goal is to optimize asset usage, maximize value, and support business operations helping the organization to get the most value out of its investments.
Technology asset management provides several benefits for organizations, including:
- Improved financial management: Organizations can track their technology spending and identify areas where costs can be reduced.
- Increased compliance: Helps organizations to track their compliance with regulations such as GDPR, HIPAA, ISO, SOC, and SOX and avoid fines or penalties.
- Improved risk management: Identify and mitigate technology risks, such as the risk of unauthorized access to sensitive data, internally and externally.
- Enhanced decision-making: Provides organizations with data related to the devices’ end-of-life and obsolescence rate which they need to make informed decisions about their technology investments.
- Support business continuity: Helps organizations ensure that their assets are available when they are needed. It identifies, tracks, and minimizes the impact of data loss leading to data continuity.
Understanding Internal and External Compliance Policies
Compliance guarantees that organizations adhere to industry-specific regulations and conform to these regulations by emphasizing internal controls. Regulatory conformity focuses on abiding by legal regulations and failure to comply may result in legal consequences.
Examples of external regulatory compliance standards
- General Data Protection Regulation (GDPR): The GDPR is a European Union regulation on Information privacy in the European Union and the European Economic Area and is a law that sets guidelines for the collection and processing of personal information from individuals. The GDPR requires organizations to diligently protect personal data, as well as provide proof about how that data is protected.
- Health Insurance Portability and Accountability (HIPAA): HIPAA is a federal law that requires the protection of sensitive patient health information from being disclosed such as individuals' medical records and other individually identifiable health information. The main objectives of HIPAA are to protect privacy, ensure security, facilitate and streamline health transactions, and enforce accountability.
- International Organization for Standardization (ISO): ISO is an independent, non-governmental, international organization that develops standards to ensure the quality, safety, and efficiency of products, services, and systems. By adhering to your ISO standards, you will ensure the seamless continuation of business operations without any disruptions to your daily processes.
- System and Organization Controls (SOC): More specifically, SOC 2 reports are crafted to assess a service organization's management of controls related to non-financial aspects like data security, privacy, and confidentiality. These reports evaluate adherence to the Trust Services Criteria, which cover security, availability, processing integrity, confidentiality, and privacy.
Compliance with regulatory mandates bears significant importance as it serves to safeguard your organization's data, uphold the confidentiality of client information, enhance your corporate standing, and mitigate overarching cyber vulnerabilities. Adhering to regulatory compliance standards is essential to ensure legal and ethical operations, fostering trust with stakeholders and safeguarding sensitive data. It also mitigates the risk of financial penalties and reputational damage that can arise from non-compliance.
Examples of internal compliance standards
In addition to meeting external regulatory compliance standards, your organization will also need to adhere to internal compliance. Internal compliance involves implementing and following internal controls, policies, and procedures related to technology asset management. These may include:
- Asset inventory management: Maintaining accurate and up-to-date records of all technology assets owned by the organization.
- Change management: Following documented processes for making changes to technology assets, such as hardware or software upgrades or installations.
- Access controls: Implementing proper access controls to ensure that only authorized individuals have access to assets and sensitive data.
- Data security: Protecting technology assets and the data they contain through measures such as encryption, firewalls, and regular security assessments.
- Documentation and record keeping: Properly documenting asset management activities, including asset procurement, disposal, and maintenance.
By achieving both internal and external compliance, organizations can demonstrate their commitment to technology asset management and mitigate risks associated with non-compliance.
Understanding the Roles of Regulatory Compliance in Technology Asset Management
Regulatory compliance defines the aim that an organization strives to accomplish. Regulatory compliance also plays a critical role in asset management, ensuring that organizations adhere to laws, regulations, and industry standards related to the management and security of assets.
Roles of regulatory compliance in managing assets:

How to Create and Implement an Asset Compliance Policy
Creating and implementing an asset compliance policy will bring numerous benefits to your company. Not only will it ensure that your organization is adhering to the necessary regulations and industry standards, but it will also strengthen your reputation, protect your stakeholders' interests, and improve operational efficiency. Here are the steps to follow:
- Assess Regulatory Requirements: Start by identifying the relevant regulations, industry standards, and legal requirements that apply to your organization's asset management. Determine which regulations are applicable to your organization based on its size, location, and nature of operations.
- Identify Policy Objectives: Define objectives and achieve them through your policy, such as data security, risk mitigation, legal compliance, and operational efficiency. Ensure that the policy aligns with your organization's overall goals and objectives.
- Establish Policy Scope: Define the scope of the policy by specifying the assets it covers. Identify the departments or individuals responsible for managing and maintaining these assets.
- Define Roles and Responsibilities: Identify the key stakeholders and their roles in implementing the policy. This may include IT personnel, compliance officers, asset managers, legal representatives, and other relevant staff. Outline the responsibilities and accountabilities of each role to ensure a clear understanding of compliance expectations.
- Develop and Document Policy Procedures: Develop and document clear and concise policy statements that outline expected behavior and procedures that support the implementation of policy. Policy statements should cover areas such as asset acquisition, allocation, usage, maintenance, disposal, data security, access controls, change management, and documentation.
- Implement Training and Awareness Programs: Develop training materials and conduct regular training sessions to educate employees about the technology asset compliance policy.
- Establish Monitoring and Enforcement Mechanisms: Define how compliance with the policy will be monitored and enforced. Implement regular audits and assessments to ensure adherence to the policy. Establish mechanisms for reporting non-compliance incidents and handling violations.
Review and Update the Policy: Periodically review and update the policy to reflect changes in regulations, industry standards, or organizational requirements. Ensure that the policy remains current and effective in addressing emerging risks and challenges in asset management.
Data Security Benefits of Asset Compliance
By focusing on asset compliance, organizations can establish a solid foundation for data security, reduce the risk of breaches and regulatory penalties, and protect sensitive information throughout its lifecycle.
- Enhanced Data Governance: Asset compliance policies promote better data governance practices within an organization. They establish guidelines for data retention, data quality, and data lifecycle management, ensuring that data is properly managed.
- Improved Incident Response and Recovery: Asset compliance policies typically include provisions for incident response and recovery in the event of a security breach or data incident by having predefined procedures and protocols in place, organizations can respond swiftly and effectively to contain breaches, mitigate damages, and restore operations.
- Reinforced Vendor Management: Asset compliance policies often address the security requirements for third-party vendors or partners who have access to an organization's assets or data. By implementing these measures organizations can ensure that vendors meet specific security standards, protecting against potential vulnerabilities introduced by external parties.
- Strengthened Security Culture: Implementing asset compliance policies helps foster a security-conscious culture within an organization. Through employee training and awareness programs, organizations can educate their workforce about the importance of data security and their responsibilities in maintaining compliance.
How often should Asset Compliance be Re-Evaluated?
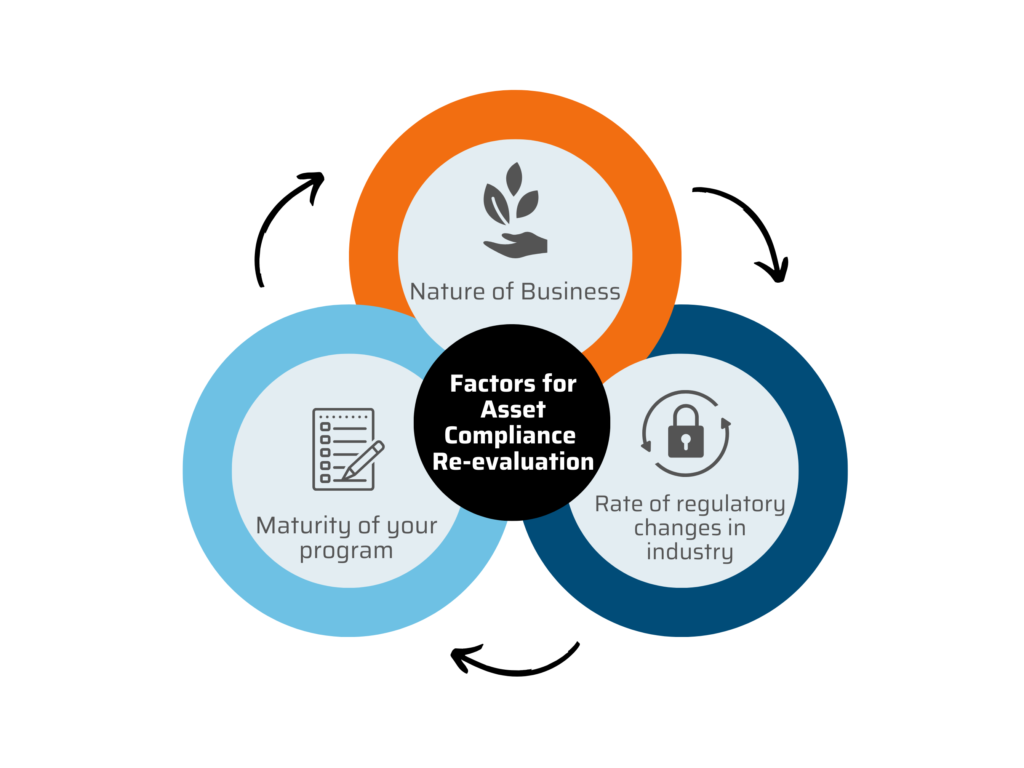
Asset compliance should be re-evaluated periodically to ensure its effectiveness and alignment with changing regulations, industry standards, and organizational needs. The specific frequency of re-evaluation can vary depending on factors such as the nature of your business, the rate of regulatory changes in your industry, and the maturity of your compliance program.
To avoid penalties for failing to meet constantly evolving market trends, organizations should reassess their quality standards. By staying up to date with changes and implementing them promptly, management can ensure compliance with the latest standards and avoid potential penalties. Periodically reviewing quality standards can also help prevent penalties resulting from non-compliance with changing market trends.
Looking to get an Asset Management and Compliance solution? See how Apexa iQ can identify your non-compliant devices in minutes.
Contact us to see the Apexa iQ platform and see why an Asset Management & Compliance solution like ours is the best fit for you.


